SINGAPORE - The authorities have stepped up the fight against the fraudulent use of Singpass to set up bank accounts or phone lines for scams by tapping the app’s user data not just for investigations, but also to pre-emptively stop potential scams in their tracks.
When necessary, data collected by the app will be used for early detection and fraud analytics to investigate and prevent criminal activity or any cyber-security incident, the Smart Nation and Digital Government Office (SNDGO) told The Straits Times on Friday.
This is regardless of whether there is suspicion that the account is being used for criminal activity, and if the disclosure of such data can be potentially incriminating, according to the March 30 update reflecting the increased surveillance, which users were notified about in their Singpass inbox.
The changes aim to protect users from fraudsters phishing for Singpass credentials and misusing them to make unauthorised withdrawals from a victim’s Central Provident Fund (CPF) account or open bank accounts, said an SNDGO spokesman.
The app’s change log said: “Clause 4.5 was amended to clarify that data may also be used, disclosed and processed for purposes of preventing any cybersecurity incident. (It) was also amended to clarify that the use, disclosure or processing may occur even if the disclosure may be potentially incriminating.”
The update expands the clause to include cybersecurity risks and increased surveillance across the app’s users, even if it leads to criminal activity being found in spite of a lack of suspicion. The clause previously stated that data collected from users may be used to prevent or investigate any fraud, unlawful or criminal activity, omission or misconduct within an account.
When scam activities are detected, Singpass will share the timestamp of suspicious transactions or other necessary information with partners including the police, the CPF Board and banks, to promptly investigate and stop potential scams, said the spokesman.
“If necessary, the Singpass team will help suspend the Singpass account to protect the user and notify the user.”
The spokesman added that the updates to Singpass are not linked to TraceTogether and that the app does not collect location data apart from the user’s IP address, to determine if the user is overseas. This gives users the option of blocking their Singpass from overseas access, he added.
Data collection on TraceTogether caused a stir in 2021 when it was revealed that the data collected could be used in criminal investigations, despite earlier assurances that the data was only for Covid-19 contact tracing. The app was stepped down in February as contract tracing efforts eased.
The changes to Singpass come after the authorities discussed ways to curb the abuse of Singpass and crack down on money mules who knowingly give up control or sell their login details for scams.
The police have arrested a “large number” of money mules for facilitating scams, but many of them are let off the hook and cannot be prosecuted.
This is because there are difficulties in proving their intent to facilitate such scams, said Law and Home Affairs Minister K. Shanmugam in a written reply to Parliament in February.
Singpass is used by some five million people here. Its auto-fill feature for digital forms, MyInfo, facilitates at least 300,000 transactions daily, across hundreds of digital services offered by the Government and approved private organisations.
It is understood that Singpass credentials have also been misused to register for prepaid SIM cards for local phone numbers. This allows fraudsters to make calls without the +65 prefix – a telltale sign that the calls are from overseas – to trick victims into trusting the caller and answering the phone.
Phone users have been reminded to be wary of calls with a “+” prefix, which was introduced by telcos in 2020 as an anti-scam measure to indicate calls from overseas. Calls from local lines made from overseas display the +65 Singapore country calling code.
The number of scam calls without the “+” prefix has risen, said Singtel, which is investigating the matter. Ms Anna Yip, chief executive of Singtel’s Singapore consumer business, said: “Recently, we have observed a small number of scam calls that appear to be from local numbers.”
The police are also investigating such calls, said a spokesman.
“As the scammers have access to telephony services provided by third parties, even if the calls come without ‘+’ prefix, the public should remain vigilant.”
The spokesman added that those receiving such calls should be alert to the demands of the callers and install the ScamShield app, which flags suspicious calls based on a database of blacklisted contacts.
Scam calls without the +65 prefix are likely by fraudsters who have purchased prepaid SIM cards from illegal sellers online, said Mr Zafar Astanov, who is from cybersecurity firm Group-IB’s fraud protection team.
He highlighted an example of pre-registered SIM cards on Facebook Marketplace sold at $55.
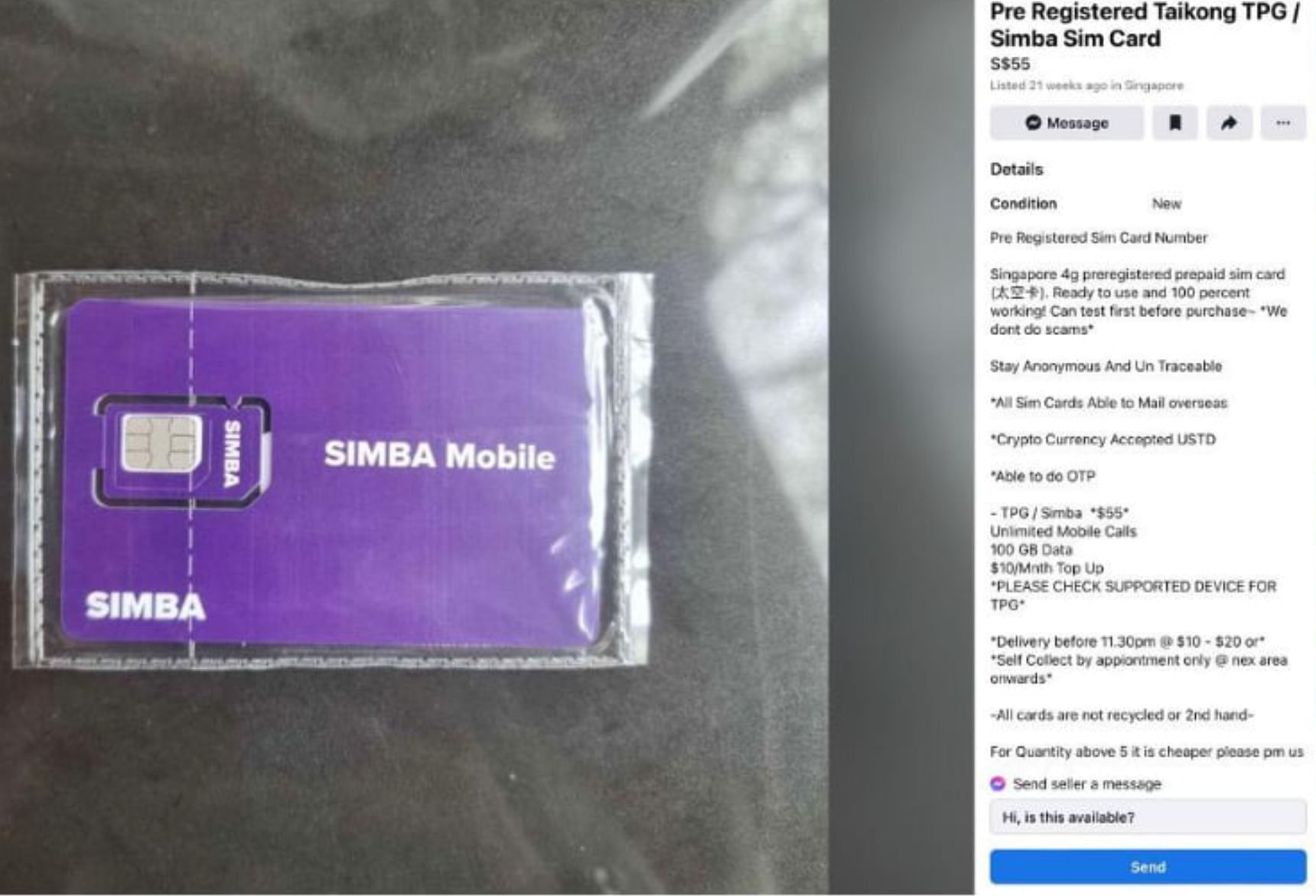
“(Scammers may use) a fake ID to register several SIM cards, or conspire with others who are willing to purchase SIM cards on their behalf,” said Mr Astanov, who is the firm’s head of pre-sales and engineering.
Victims may receive calls from scammers posing as bank employees or Internet providers with a seemingly legitimate local phone number to avoid suspicion. This makes it harder to know whether a call is a scam, he added.
“To appear more credible, fraudsters might also provide a few of your details, such as name, phone number and even the bank you have an account with. Personal records are actively traded on the Dark Web marketplaces.”
The scammers then typically talk the victim into transferring money or giving their credentials under the guise of potential fraud, said Mr Astanov. Victims should hang up and call the number on the back of their credit card to validate the information, he added.
Mr Ryan Phung, 40, was among several people who were tricked into picking up scam calls that did not have the +65 prefix.
In February, in one of the three occasions that he received such calls, the software business owner was told that he had pending transactions with a bank and was asked for his NRIC number and name.
Mr Phung hung up and called the bank, which verified that the caller’s claims were false.
When she received a call without the +65 prefix, Ms Grace Tan, 36, thought it could be from a courier as she had been expecting a parcel.
She heard an automated message when she answered the phone, but was soon directed to a Mandarin-speaking man, who hung up the moment Ms Tan asked to speak in English.
Those involved in the misuse of Singpass have been hauled to court.
They include 36-year-old Sazali Karim, who was charged in February with selling his Singpass details, which were allegedly used by scam syndicates to create new bank accounts. He is said to have received $8,000 for his details.
Last August, two teens were convicted of selling their Singpass details to scammers to open HSBC and Standard Chartered Bank accounts for money laundering. The pair were among eight suspects who were arrested in June for their roles in a spate of phishing scams where at least 60 victims lost more than $60,000.
Under the Computer Misuse Act, those found guilty of disclosing their Singpass information for wrongful gain can be jailed for up to three years and fined up to $10,000.


